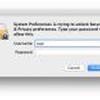
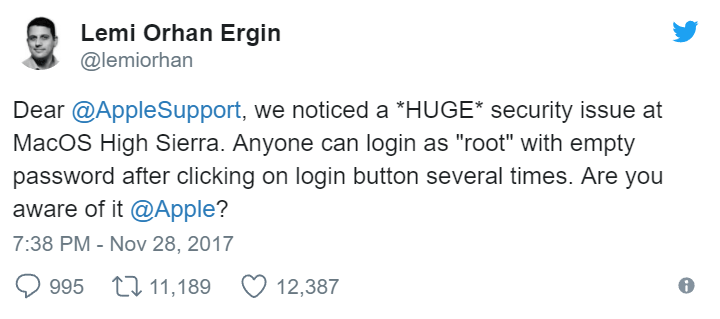
A developer, last night, reported a security problem in macOS High Sierra. This is the latest revision of the operating system for Apple computers. It is possible to log in without a password and obtain 'administrator rights', giving you full access to the computer.
It is as simple as it is: you log in as admin with no password required. The bypass works by putting the word "root" (without the quotes) in the user name field of a login window, moving the cursor into the password field, and then hitting enter button with the password field empty. With that—after a few tries in some cases—the latest version of Apple's operating system logs the user in with root privileges.
The vulnerability seems to be really simple and can easily be exploited by malicious software, or a virus, to gain admin rights. The second scenario, one can gain access to macOS more easily, you just need physical access to the PC. I see a lot of happy students at school now (and a lot of worries system admins).
Apple representatives issued the following statement:
We are working on a software update to address this issue. In the meantime, setting a root password prevents unauthorized access to your Mac. To enable the Root User and set a password, please follow the instructions here: https://support.apple.com/en-us/HT204012. If a Root User is already enabled, to ensure a blank password is not set, please follow the instructions from the "Change the root password" section.
Specifically, users should do the following:
- open the Users & Account menu in System Prefereces
- click the padlock at the bottom and enter an administrator name and password
- click Login Options
- Click Join (or Edit)
- Click Open Directory Utility
- Click the padlock at the bottom and enter an administrator name and password
- From the menu bar in Directory Utility, choose Edit > Change password
- Enter a strong password
The most important part for now is not to disable the root account. That only allows the root account to be re-enabled by putting "root" in a user name field and leaving the password blank. Until Apple issues a patch, people should secure the root account with a strong password and leave the account enabled. As always, passwords should be at least 13 characters long, randomly generated, and contain a mixture of numbers, upper- and lower-case letters, and symbols. As an added layer of security, users should also ensure they have filevault turned on.
High Sierra was released on 25 September for Mac computers. The most recent version, 10.13.1, appeared on October 31 and contains the vulnerability.
Apple vulnerability: root login without password possible