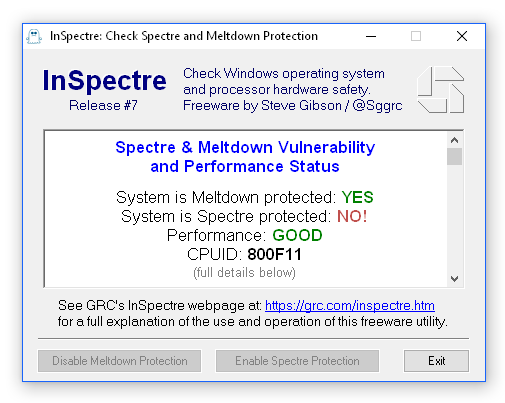
This application is made by security researcher Steve Gibson. To fully protect against both attacks, users have to update both their BIOS and operating system. This can have a negative impact on performance, depending on the tasks performed on the computer. InSpectre shows which updates have been installed and what has to be done to protect the system against the attacks. The tool also makes it possible to enable or disable protection against Spectre and Meltdown.
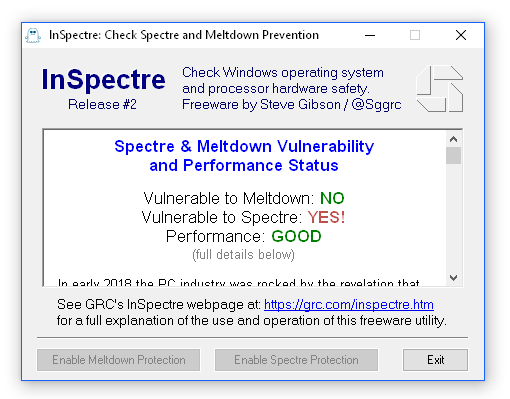
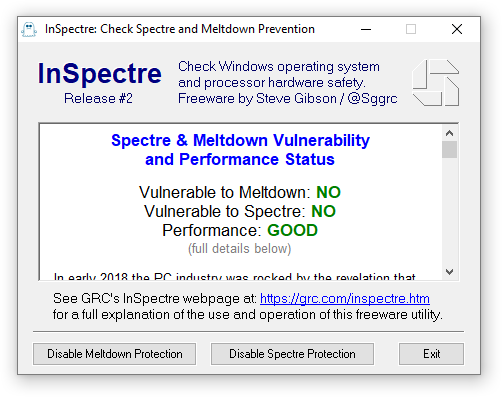
In early 2018 the PC industry was rocked by the revelation that common processor design features, widely used to increase the performance of modern PCs, could be abused to create critical security vulnerabilities. The industry quickly responded, and is responding, to these Meltdown and Spectre threats by updating operating systems, motherboard BIOSes and CPU firmware.
Protection from these two significant vulnerabilities requires updates to every system's hardware–its BIOS which reloads updated processor firmware–and its operating system–to use the new processor features. To further complicate matters, newer processors contain features to minimize the performance impact of these important security improvements. But older processors, lacking these newer features, will be significantly burdened and system performance will suffer under some workloads.
This InSpectre utility was designed to clarify every system's current situation so that appropriate measures can be taken to update the system's hardware and software for maximum security and performance.
Gibson warns that his tool is new and that conclusions on the output of the tool should be carefully considered as he writes, “it has been carefully tested under as many different scenarios as possible. But new is new, and it is new. We may well have missed something. So please use and enjoy InSpectre now.
“But you may wish to check back in a few days to see whether we may have found and fixed some last bits of debris,” Gibson adds.
Change Info:
Release #8 — Now shows whether an Intel microcode patch is (ever) available for Spectre.
Intel has finished designing microcode update patches for its processors. On April 2nd, 2018, they announced that processors that have not yet been patches will never be patched. Their full statement is available in this PDF document. In that document, Intel specifies which of their many processors do have patches and which of their more recent processors will never receive updated firmware. Now that the industry has this information, this 8th release of InSpectre incorporates that list of CPUIDs and displays whether microcode firmware updates exist for the system's Intel CPU.